| �Editor's Note |
| �Free Software |
| �GPG |
| �IEEE 802.11a |
| �Linux |
| �MBSA |
| �METU-CC Web Site |
| �Thesis Advisor A. Prog. |
| �Viruses |
| �CISN Archive |
| �Questionnaire |
| �Send Feedback |
| Microsoft Baseline Security Analyzer | |
|
Microsoft Baseline Security Analyzer (MBSA) is a tool designed to scan for the security vulnerabilities of computers with Windows NT4, Windows 2000, Windows XP Professional, and Windows XP Home Edition operating systems. MBSA is not a security solution for only operating systems. At the same time, for applications such as Internet Information Services (IIS), SQL Server, it performs the required updating procedures and tests ensuring the safety. MBSA uses HFNetChk tool to confirm that security updates are being performed. MBSA not only checks the system for security vulnerabilities, but it also checks the system for weak password use, misconfigured servers like IIS and SQL Server and sends warning messages about the configurations of Microsoft Office, Outlook and Outlook Express. Another feature of MBSA is that it scans the operating systems on the local network. To be able to analyze the other computers for security vulnerabilities, MBSA requires the administrator login name and password on the computer it is installed. Local network computers that the administrators are responsible from can be scanned and precautionary measures can be taken for vulnerabilities found. MBSA programını aşağıdaki adresten indirebilirsiniz: Usage: 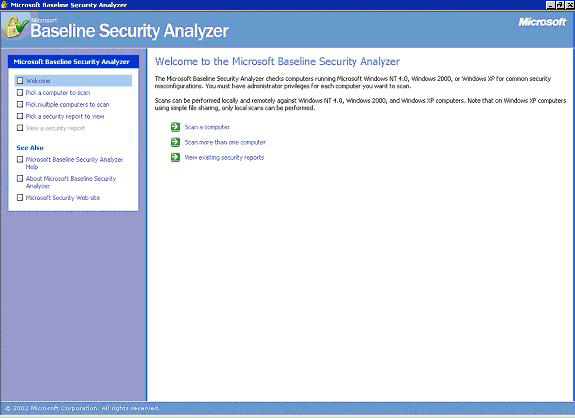
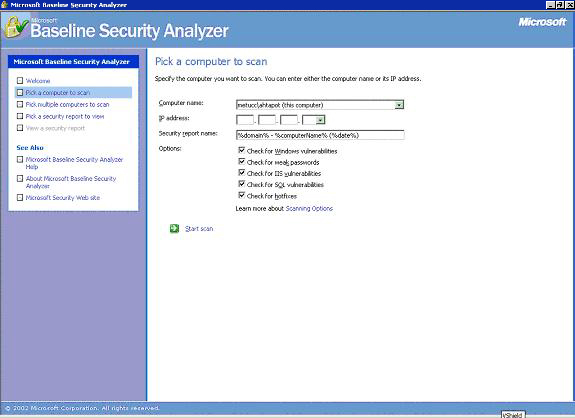
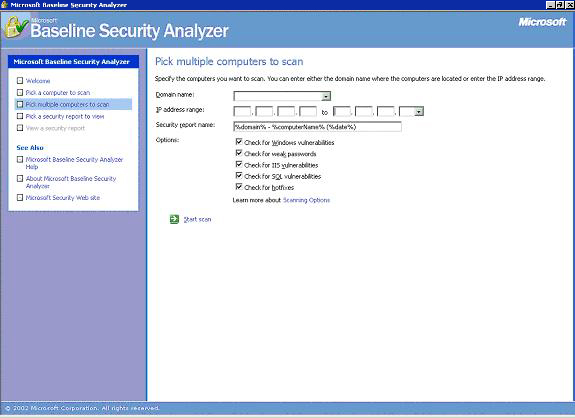
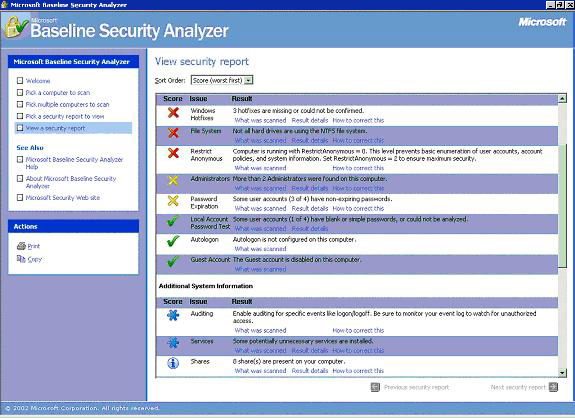
"Scan a computer": This is the simplest mode. It enables to scan the computer itself or one computer on the network. "Pick a computer to scan" option scans the network with regard to the IP number or computer name. If this option is selected, it displays the name of the computer in the "Computer name:" field. On this field, the name of the remote computer on the network or in the field below the "IP address:" the IP of the remote computer can be entered to scan a remote computer. "Scan more than one computer": "Pick Multiple Computer to Scan" option enables scanning of computers in a domain or IP address interval. It should be noted that to scan the remote computers, MBSA requires the administrator login name and password on the computer it is installed, authorizing the program to scan other remote computers on the network. Analyzing the Results: Analyzing the results is not a difficult task. The graphical interface makes it easier to see the vulnerabilities as well the strong issues about the system. Red signs indicate serious vulnerabilities Yellow signs indicate vulnerabilities of significance, but secondary to red ones. They inform about misconfigurations that may turn out to be vulnerabilities Green sign indicates that there are no vulnerabilities regarding that feature. Blue star and letter "i" in a circle both provide information that may be useful. More detailed information about vulnerabilities can be reached from the "What was scanned" link available under the explanation.. "Result details" link displays these vulnerabilities and other links if necessary. "How to correct this" link explains how that vulnerability can be corrected. İbrahim Çalışır |
||
| - TOP - |
Design: CC - INFO